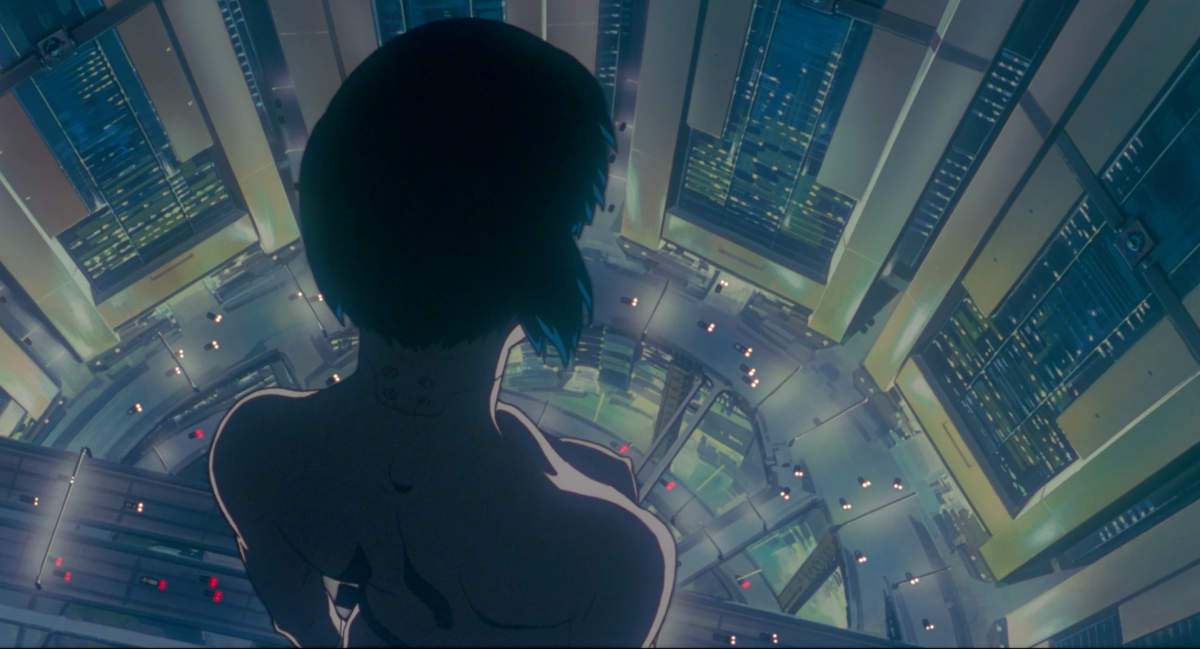
The year is 2030. An “infamous mystery hacker” known as the Puppet Master is wreaking havoc on the internet, breaking into the so-called cyber-brains of several humans as well as “every terminal on the network.” As it turns out, the Puppet Master is a creation of Japan’s Ministry of Foreign Affairs.
In other words, the Puppet Master is what we would call today a government-backed hacker, or advanced persistent threat (APT). In this case, however, the “phantom” hacker goes rogue and is wanted for “stock manipulation, spying, political engineering, terrorism, and violation of cyber-brain privacy.”
That is the basic premise of the Japanese anime cult classic Ghost in the Shell, which marked its 30th anniversary this week since its debut, and was based on the chapters titled Bye Bye Clay and Ghost Coast from the first volume of the eponymous manga, released in May 1989.
To say that the story of the Puppet Master was ahead of its time may be an understatement. The World Wide Web, essentially what flourished from the internet as we know it today, was invented in 1989, the same year that the first volume of Ghost in the Shell’s manga — including the story of the Puppet Master — hit newsstands in Japan. (The World Wide Web publicly launched in 1991.)

In the manga, when the Puppet Master gets caught, an official from Public Security Section 6, an agency under the Ministry of Foreign Affairs, explains that they had been after the hacker “for a long time,” and they “profiled his behavioral tendencies and code/tech patterns.”
“As a result, we were finally able to create a special anti-puppeteer attack barrier,” the official says in the manga.
At the risk of extrapolating too much from a couple of sentences, the reality is that what the official is describing is basically what cybersecurity companies, such as antivirus firms, do everyday to stop malware. Not only do they create so-called signatures based on the malware’s code, but also based on its behavior and properties, known as heuristics.
There are other elements of the plot that turned out to be prescient.
At the beginning of the Puppet Master investigation, Major Motoko Kusanagi, the protagonist and commander of the counter-cyberterrorism unit Section 9, hacks into the network of the Sanitation Department to track a garbage truck. (These days, government hackers who work for intelligence agencies often break into large networks to spy on specific individual targets, rather than to siphon data out of the hacked network itself.)
While that happens, one of the garbage men confesses to his colleague that he hacked into his wife’s cyber brain because he thinks that she is cheating on him. Right after, we find out he’s been using a computer virus he got from “some programmer.” This is a clear case of tech-enabled domestic abuse, or even stalkerware, which TechCrunch has investigated extensively over the last few years.
As it turns out, the abusive garbage man had no wife. His memories were all made up. His ghost — essentially his mind or consciousness — was hacked by the Puppet Master with the goal of using him to hack into government officials. In some way, that’s similar to what some advanced hackers do when they hack into networks that they then use to hack their actual target, as a way to hide their tracks adding separation from themselves and the final target.
The Puppet Master as a government hacker, the breaching of networks to track targets or use them to then attack other networks, and a jealousy-fueled hack are not the only fascinating bits of speculative fiction related to hacking in the anime.
John Wilander, a cybersecurity veteran who writes hacker-themed fiction books, wrote an exhaustive analysis of the movie that highlighted details referencing real-life scenarios. Wilander gave examples, like hackers reusing known exploits or malware to make attribution more difficult, investigating malware without alerting the authors and infecting yourself with it, and using computers for industrial espionage.
Obviously, the manga and anime take the basic — and realistic — premise of the Puppet Master as a hacker into more fantastical directions. The hacker, which turns out to be an advanced artificial intelligence, can control humans through their cyber-brains, and is self-aware to the point that — spoiler alert — it asks for political asylum and ends up proposing to Kusanagi to fuse their “ghosts,” essentially their minds.

To understand how prophetic Ghost in the Shell was, it’s crucial to put it in its historical context. In 1989 and 1995, cybersecurity wasn’t even a word yet, although the term “cyberspace” had been famously coined by sci-fi author William Gibson in his classic book, Neuromancer.
Computer security, or information security, however, was already a reality, and had been for a couple of decades, but it was an extremely niche specialty within computer science.
The first computer virus is believed to be the Creeper worm, which was unleashed in 1971 on the Arpanet, the government-developed network that became the internet’s forerunner. A handful of other viruses and worms wreaked havoc after that, before they became ubiquitous once the internet and the World Wide Web became a reality.
Perhaps the very first documented government espionage campaign on the internet was the one discovered by Clifford Stoll, an astronomer by training who also managed the computers at the Lawrence Berkeley National Laboratory in California. In 1986, Stoll noticed a 75 cent accounting error in the network, which eventually led him to discover that a hacker had broken into the lab’s systems. In the end, the hacker was identified and found to have been feeding information from the lab and other U.S. government networks to the Soviet Union’s KGB.
Stoll immortalized his months-long scrupulous and painstaking investigation in the book The Cuckoo’s Egg, a first person account that reads like a very detailed and extensive report by security researchers analyzing a hacking campaign carried out by government hackers. The Cuckoo’s Egg has since become a classic, but it’s probably fair to say it didn’t exactly hit the mainstream when it was released.
As far as I can tell, Ghost in the Shell’s creator Masamune Shirow never spoke about what real life events inspired the hacking plot points in the manga. But it’s clear that he was paying attention to what, at the time, was a hidden world that was alien to most people on Earth, who were still years away from being online, let alone being aware of the existence of hackers.